Risk Management Enterprise Fundamentals Explained
Table of ContentsThe Basic Principles Of Risk Management Enterprise Risk Management Enterprise Fundamentals ExplainedAbout Risk Management Enterprise
Control that can check out or edit these elements by establishing details access legal rights for specific users, guaranteeing info protection and customized usability. Permits individuals to tailor their interface by picking and preparing crucial information aspects. Gives a personalized experience by permitting customization of where and how information aspects are shown.It permits access to real-time integrated information quickly. Centers can use detailed information knowledge for quicker and more educated decision-making.
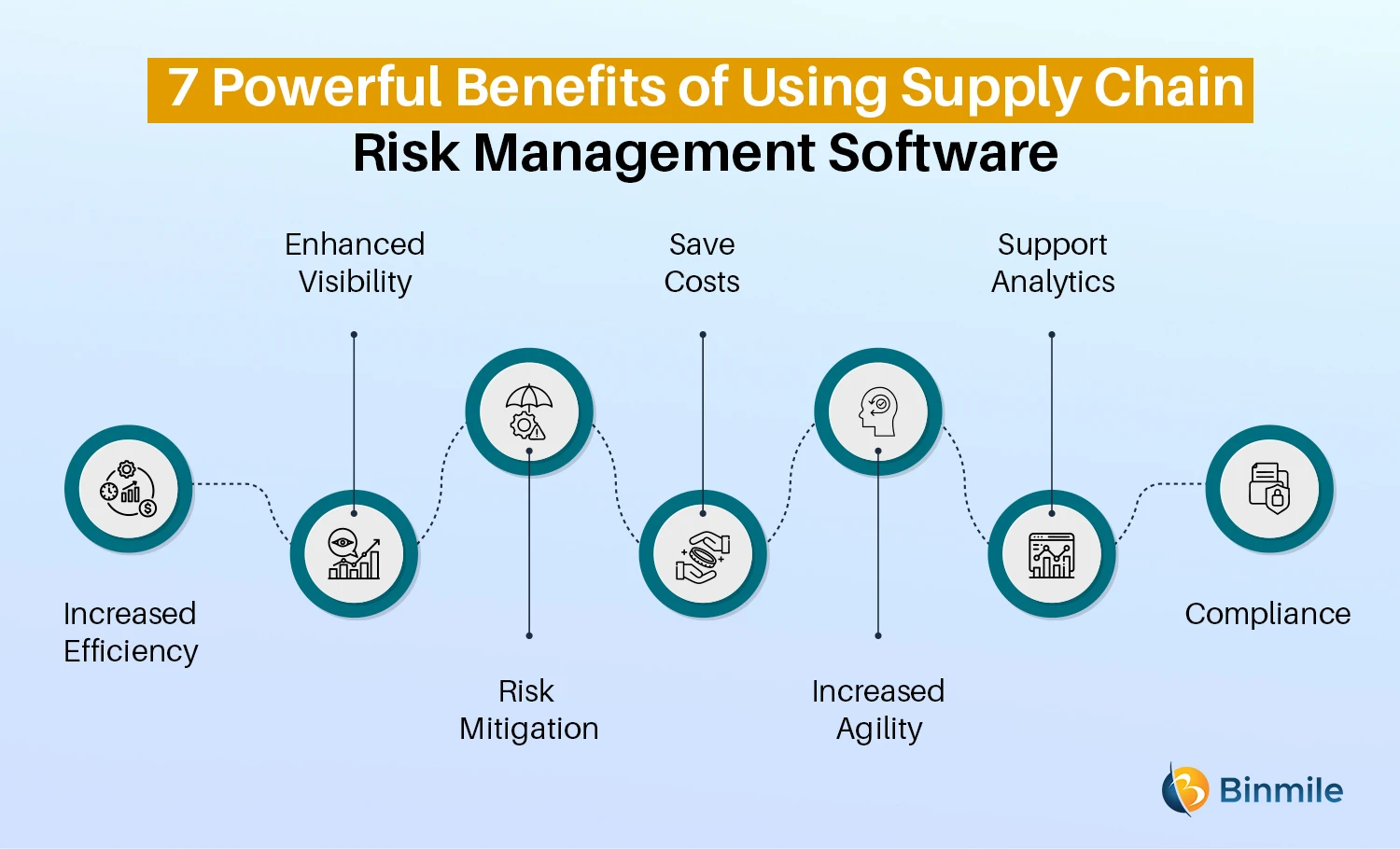
Diligent is a danger management software program that allows enhancing efficiency, and enhances development. It likewise aids keep track of threats with ERM software that consists of incorporated analytics and adapts to your organization needs. This software application features various valuable features. Below we have actually highlighted the most vital ones. So, inspect them out.
Things about Risk Management Enterprise
Simplifies the process of accumulating danger information from numerous components of the organization. Provides management and the board with real-time threat insights. Use ACL's innovative analytics to spot risk patterns and forecast threats.
This allows business to record risk understandings and red flags in the third-party vendor's safety report. Makes it possible for companies to catch and record risk understandings and red flags in third-party vendor safety reports.
Identifying dangers in breakthrough aids a facility plan for audits. It additionally decreases risk with structured conformity and risk administration. Due to this facilities will not need to handle various systems for threat tracking. The individuals of Hyperproof can systematize threat administration in one area. It can aid gather and track all your dangers in the Hyperproof danger register.
It makes sure that every little thing is arranged and obtainable for auditors. Utilizes automation to keep evidence up-to-date while decreasing hands-on initiative. It supplies quick access to needed info and documentation. This makes sure the safety and security of Hyper proof instances by allowing multi-factor authentication (MFA) using authenticator applications such as Google Authenticator, Microsoft Authenticator, or Authy.
An Unbiased View of Risk Management Enterprise
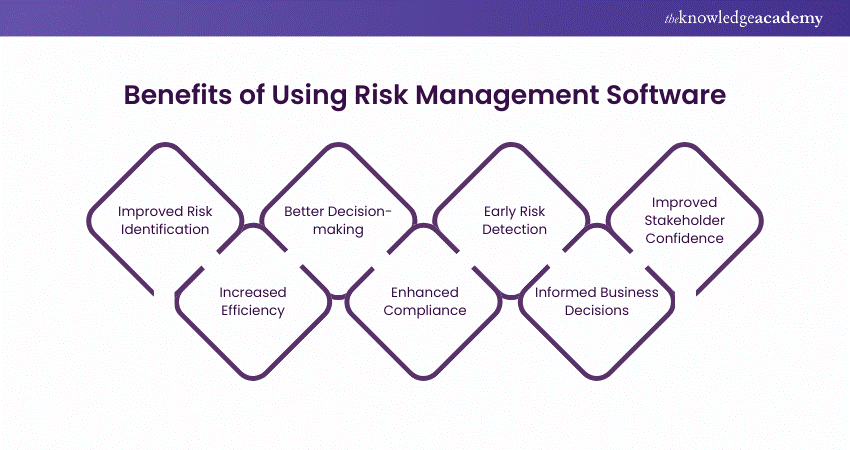
It gives top-tier protection functions to guard delicate information. This threat administration software is an ideal click here tool for facilities looking to fix unneeded problems or threats.
Individuals can also use the AI-powered devices and pre-existing material to produce, evaluate, prioritize, and address threats effectively. Enhances the procedure of configuring and occupying threat signs up. Makes use of AI and collection content to improve danger analysis precision. It makes it possible for much faster recognition and mitigation of dangers, This is primarily an aesthetic design.